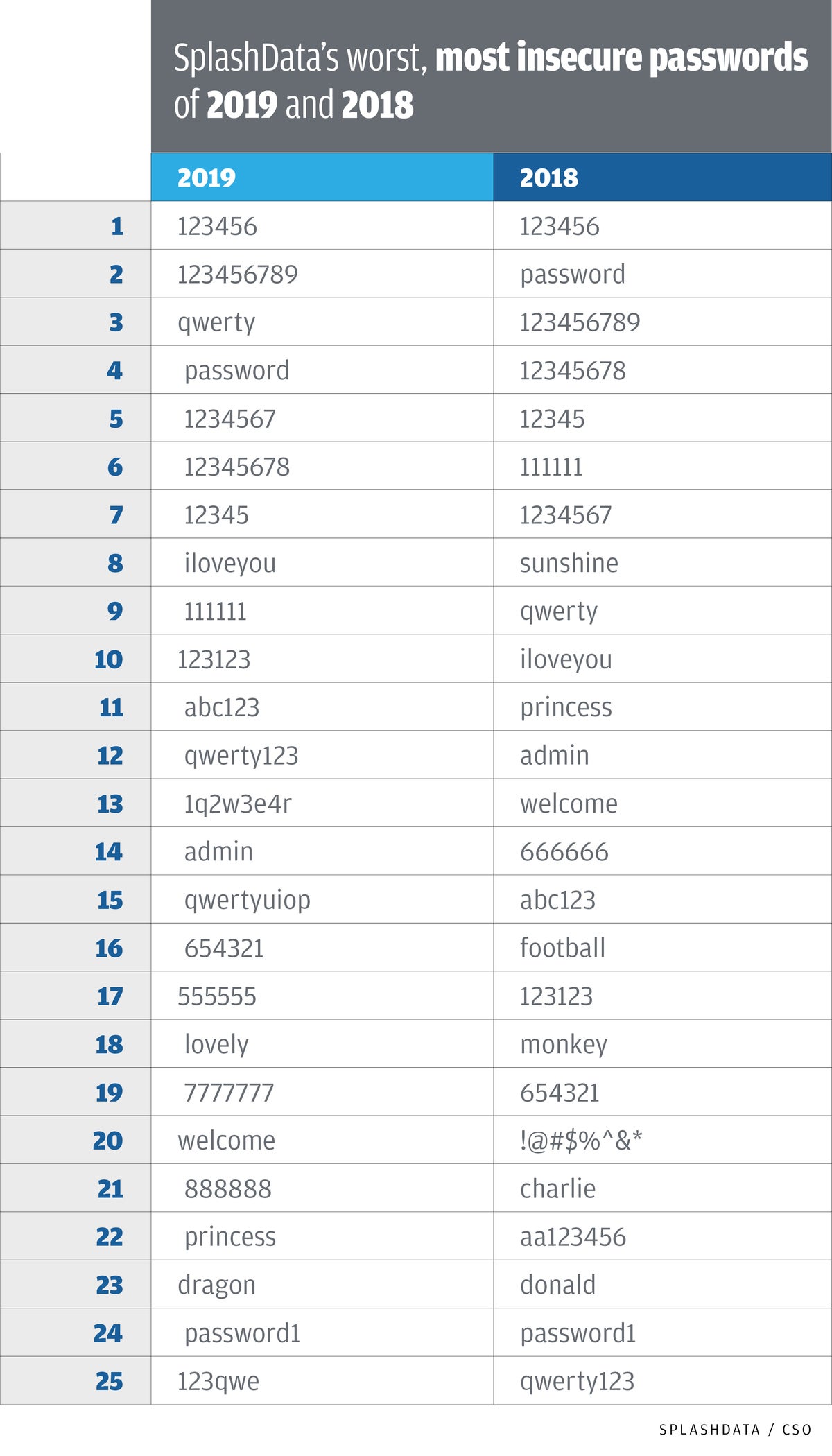
Pop quiz: What has been the most popular — and therefore least secure — password every year since 2013? If you answered “password,” you’d be close. “Qwerty” is another contender for the dubious distinction, but the champion is the most basic, obvious password imaginable: “123456.”
Yes, tons of people still use “123456” as a password, according to SplashData’s top 25 most common passwords. It ranked second place in 2011 and 2012 and has been number one every year right through 2019. SplashData’s list is based on the company’s analysis of millions of passwords leaked on the internet.
Plenty of other epically insecure passwords continue to make SplashData’s annual password hall of shame, including the aforementioned “password” (always in the top five, and No. 1 in 2011 and 2012); “qwerty” (always in the top ten); and a slightly longer variation of the reigning champ, “12345678” (always in the top six).
“Disappointingly, there are no big differences between recent worst password lists and this year’s,” says Morgan Slain, SplashData’s CEO. That’s because the passwords on the lists are mostly generated by consumers who continue to stick with passwords that are simple, easy to remember — and therefore are far too easily hacked, he says.
Worst passwords of 2019
Here are SplashData’s most popular, least secure passwords of 2019.
- 123456
- 123456789
- qwerty
- password
- 1234567
- 12345678
- 12345
- iloveyou
- 111111
- 123123
Other worst password lists from NordPass and the U.K.’s National Cyber Security Center are mostly consistent with SplashData’s findings. And a comparison to SplashData’s 2018 list shows not much change year over year.
 SplashData / IDG
SplashData / IDGWe’ve also asked cybersecurity experts for their thoughts on the problems with enterprise passwords, how to improve password and authentication security, and the possibility of a “passwordless future.”
The problems with enterprise passwords
Businesses are increasing the use of multi-factor authentication (MFA) and single sign-on (SSO) services to bolster security. Nonetheless, Too many employees “still have poor password hygiene that weakens the overall security posture of their company,” according to the 3rd Annual Global Password Security Report (2019) from LogMeIn.
It’s no wonder why many employees have password fatigue, which in turn leads to lax password security. LogMeIn’s report finds that users at larger companies (1,001 to 10,000 employees) have on average 25 passwords with which to contend. The problem is more acute for users at small businesses (25 or fewer employees), who have on average 85 passwords to juggle. Employees in the media/advertising industry use the greatest number of passwords — 97 — on average, compared to 54 passwords per employee in government (the sector with the lowest average number of passwords per employee).
“Passwords have traditionally been the first line of defense for companies, but they continue to cause frustration and risk,” says John Bennett, general manager of identity and access management at LogMeIn. “Even more, password sharing and reuse remains a common practice in most businesses, with employees reusing one password an average of 13 times.”
Shadow IT presents another challenge. “One of the biggest problems plaguing enterprise password security is shadow IT, wherein employees use third-party apps, services and devices without IT oversight to more efficiently do their jobs,” says Matt Davey, chief operating officer at password management software company 1Password. “As employees continue to find their own productivity hacks, the ‘solve your own problem’ mentality leads to unseen passwords that have no IT oversight.”
All told, the password problem brings significant risks to enterprises. Verizon’s 2019 Data Breach Investigations Report finds that 80% of data breaches can be traced to weak or compromised passwords.
How to improve enterprise password security
Require the use of a password manager
Password management applications for business users (such as 1Password, Dashlane and LastPass) are an effective first step toward reducing security risks associated with passwords, notes Dr. David Archer, principal scientist of cryptography and multiparty computation at security research and consulting firm Galois. He recommends having enterprise users leverage password managers to generate and store lengthy passwords with all alphabet options (such as mixed-case letters) turned on. With a password manager in place, users should have only two passwords they need to remember, he adds: the password to the password manager app and the password to the computer account a user logs into every day.
Require the use of MFA
MFA factors include what you know (a password), what you have (a device, such as a smartphone), and who you are (a fingerprint or facial recognition scan). Using MFA to require verification, such as a code sent to a mobile device, in addition to the use of strong, unique passwords, can help provide better enterprise protection, says Justin Harvey, global incident response lead at Accenture Security.
Don’t let users create passwords with dictionary words
In a brute-force dictionary attack, a criminal uses software that systemically enters every word in a dictionary to figure out a password. To thwart such attacks, many experts recommend against using words that exist in a dictionary.
Steer users away from passwords that include information about them
Don’t use the names of a spouse, pet, city of residence, birthplace or any other personally identifiable information in a password, as that information could be deduced from the user’s social media accounts. “A hacker is much more likely to guess your ‘pet’s name + 1234’ as your password than they are to figure out that your password is ‘D2a5n6fian71eTBa2a5er,’” says Davey.
Educate users on what makes a password safe
A safe password doesn’t appear anywhere else in the public realm (such as in dictionaries), doesn’t appear anywhere in private (such as other accounts users have), and contains enough random characters that it would take an eternity to guess the password, even when using brute-force or rainbow table techniques, says Archer.
Regularly perform password audits
Ideally, your organization should use an authentication system that allows for password audits, says Tim Mackey, principal security strategist at the Synopsys Cybersecurity Research Center (CyRC). “Look for things like password reuse across employees or use of common words or common words with simple character replacements. If you uncover a weak password, use the event as a learning opportunity for users.”
Don’t villainize mistakes
Create an environment in which employees feel comfortable raising questions or concerns about security, especially if they suspect they may have slipped up, suggests 1Password’s Davey. “Don’t villainize people,” he says, because they may be afraid to tell you when they’ve made a mistake. “If you know about security issues as they arise, you can act quickly to address the initial threat and take steps to prevent it from happening in the future.”
Require users to generate passwords with all of the character types
This includes upper- and lowercase letters, numbers and symbols, advises Shayne Sherman, CEO of online technology knowledgebase TechLoris. “Use an algorithm that compares passwords to users’ previous passwords to prevent incrementing.”
The passwordless future is imminent — or is it?
In the near future, will concerns about weak and strong passwords become irrelevant, thanks to alternative forms of authentication such as biometric facial and fingerprint scans? Some cybersecurity experts don’t buy the passwordless dream. “I don’t think we’ll ever be completely free of passwords,” says Mackey of Synopsis CyRC. “Even when single sign-on or social media authentication paradigms are used, there remains a need to identify a user. While biometric solutions offer promise, such solutions are best employed as an additional factor in a multi-factor strategy.”
Biometric authentication has its drawbacks, adds Juniper Networks’ Global Security Strategy Director Laurence Pitt. “One drawback to biometrics is that they can be stolen just as easily as someone can steal your credit card,” he says. “Another drawback is that there are other environments in which these authentication methods just aren’t feasible. This can lead people to default on password-only authentication, which isn’t enough.”
Internet of Things (IoT) devices add yet more complexity to the hope of a passwordless future, says Assaf Harel, chief scientist and co-founder at Karamba Security. “These devices usually come with easy-to-guess or search default passwords. So, they can become a playground for many botnets, such as Mirai, that look for a passive fleet of devices to serve their distributed denial of service campaigns. IoT devices require a fresh look into how to integrate multifactor authentication into single-purpose devices to make botnet recruitment efforts much more difficult.”
Yet, some experts predict we’re on our way to a passwordless future. “Change takes time, but I wouldn’t be surprised if we eventually live in a passwordless world,” says Peter Purcell, co-founder of EVAN360, a remote technology support platform. In the meantime, Purcell says security measures such as face and fingerprint scans, USB security keys and voice biometrics will increasingly give enterprises more advanced user authentication.
For example, Purcell points out that in 2017, Google began requiring all employees to use physical security keys in place of passwords and one-time codes. The company reported one year later that none of its employees had been successfully phished as a result.
Biometrics “will certainly free us from passwords and make authentication easier and more reliable,” adds McAfee CIO Scott Howitt. “In the past, the problem with biometrics, such as facial recognition, was the amount of computer horsepower needed to run systems like that. Today, these systems run in the cloud and are fast and efficient. The key is that biometrics must be easy to use as well as reliable. Users have to be able to trust that whatever biometrics they setup actually work to make their lives easier rather than more difficult.”
Ultimately, the transition to “truly passwordless authentication is going to be a journey,” says Jim Ducharme, RSA’s vice president of identity and fraud and risk intelligence products. “Today, all passwordless authentication is rooted and reliant on a password and username for account enrollment and recovery. While passwordless authentication such as face and fingerprint ID is common on many devices, accounts are still established with a password, and if your device is lost or stolen, the account is recovered using a password.”
To achieve a passwordless world, then, we need an approach that considers credential enrollment, recovery and ways for users to securely authenticate on devices that don’t support biometrics or Fast Identity Online (FIDO) capabilities.
“These new methods of authentication, combined with more secure enrollment and recovery mechanisms, and layered with risk-based authentication, are the keys to eliminating the use of passwords completely,” Ducharme says. “Or at least, they’ll allow us to dramatically reduce the complexity of a password to look more like a simple four-digit PIN.”