
The Iranian MuddyWater cyber-espionage group added new attack vectors to use as part of hacking campaigns targeting telecommunication and governmental organizations according to an analysis from the Clearsky Security threat intelligence outfit.
This happened despite the advanced persistent threat (APT) group — or government-backed hacking group — having screenshots of their server backends and one of their command-and-control (C2) server’s codebase leaked via a Telegram channel during early-May.
MuddyWatter actors have supplemented their tactics, techniques, and procedures (TTPs) with new decoy macro-powered Microsoft Word documents that drop payloads via compromised servers and new documents designed to leverage the tried-and-true CVE-2017-0199 also known as Microsoft Office/WordPad Remote Code Execution Vulnerability w/Windows API.
The documents which deliver VBA macros to the targets’ computers will download a second stage malware payload camouflaged as JPG files from hacked servers located in the same countries as the potential victims.
The ones designed to exploit CVE-2017-0199 “were identified by only three antivirus engines. This is in stark comparison to a previous attack we reported on, in which the documents were identified 32 times,” says the Clearsky Security report.
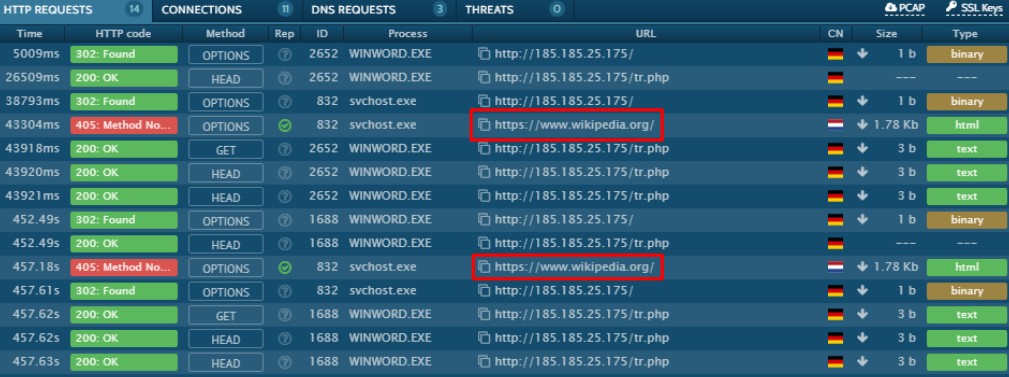
Once the victim’s computer gets compromised, the malware tries to phone home to the attackers’ C2 servers and, if the attempt fails, the victim gets redirected to Wikipedia.
To exploit the CVE-2017-0199 flaw, MuddyWatter uses two types of decoy documents, with the first one making use of error messages while the second will exploit the vulnerability right after they are opened by the victims.
The Clearsky Security researchers also found that some of the decoy files utilized by the Iranian APT were using both attack vectors.
The first exploits the Microsoft Office/WordPad RCE vulnerability, and subsequently downloads the first and second stage payloads from actor-controlled C2 servers and drops them on the targets’ machines.

MuddyWater (also known as TEMP.Zagros and SeedWorm) was first observed in 2017 and is known by experts to mainly target Midle Eastern entities.
Although quite new on the scene, this APT group is very active given that it made 131 victims in 30 organizations from late-September to mid-November 2018 according to a Symantec report from December 2018.
MuddyWater was also observed while diversifying their attacks by targeting government and defense entities in Central and Southwest Asia, as well as numerous public and privately-held organizations from Europe, Asia, and North America [1, 2, 3].

As discovered by Cisco Talos during May, the MuddyWater threat group updated their TTPs to incorporate several new anti-detection techniques designed to provide remote access to infiltrated systems while evading detection as part of a campaign dubbed BlackWater.
During the BlackWater campaign, the APT group made extra efforts to avoid detection after compromising targets by attempting to avoid Yara rules and host-based signatures using modified tools, replacing variable names used by their malicious implants but also making sure that the overall functionality and structure remained untouched.